Geopolitics Is a Defining Force in Cybersecurity
Share

Cybersecurity in 2026 cannot be separated from geopolitics. Conflicts, sanctions, trade wars, and technological rivalry are no longer distant concerns discussed only at policy tables. They now directly influence how organizations assess cyber risk, design defenses, and decide who and what they can trust.
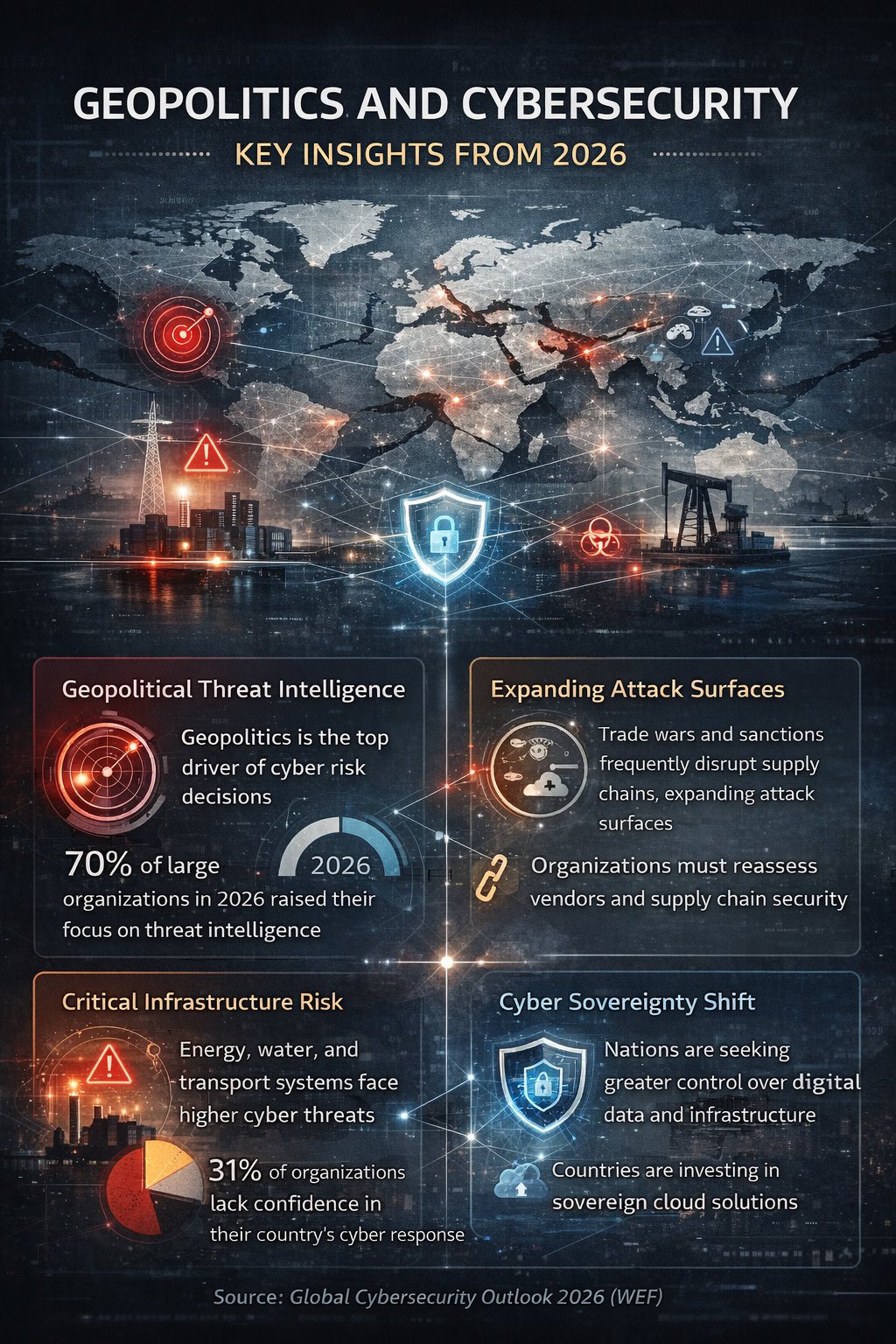
The Global Cybersecurity Outlook 2026 makes this shift unmistakable. While the percentage of organizations changing their cybersecurity strategy due to geopolitics has declined from 93% in 2023 to 66% in 2026, geopolitics remains the single most influential factor shaping cyber risk mitigation. The initial wave of reactive changes triggered by global instability has passed. What remains is a more permanent reality, where geopolitical risk is embedded into cybersecurity strategy rather than treated as a temporary disruption.
TL;DR
- Geopolitics remains the top driver of cybersecurity strategy in 2026.
- Organizations are shifting from isolated defense to intelligence-led collaboration.
- Nation-state cyber operations are tools of diplomacy and economic pressure.
- Trade wars and supply chain shifts are expanding cyber attack surfaces.
- Critical infrastructure is a prime target in geopolitical cyber conflict.
- Cybersecurity is increasingly tied to national and digital sovereignty.
From Reactive Defense to Intelligence-Driven Collaboration
As geopolitical volatility becomes a constant, organizations are moving away from isolated, perimeter-based defense models. In their place is a growing emphasis on intelligence, coordination, and shared situational awareness.
Survey respondents identified two dominant drivers reshaping cybersecurity strategies. The first is a stronger focus on threat intelligence, especially intelligence tied to nation-state activity. The second is deeper engagement with governments and information-sharing groups.
This shift is being led by large, globally exposed organizations. Companies operating across borders face greater exposure to sanctions, regulatory divergence, and politically motivated cyber operations. As a result, they are more likely to invest in collaboration and shared defense.
The data highlights a clear divide. Seventy percent of organizations with more than 100,000 employees have increased their focus on threat intelligence, compared with only 30% of organizations with 1,000 employees or fewer. Nearly half of large organizations have also deepened engagement with government agencies, while only a quarter of smaller firms report the same.
Smaller organizations often lack the staff, resources, or access needed to participate in collective security efforts. This leaves many relying on risk acceptance rather than active mitigation when geopolitical pressures rise, widening the resilience gap across the digital ecosystem.
Why Geopolitical Cyber Risk Is Harder to Predict
One of the most important insights from the WEF report is not just that geopolitical cyber risk is increasing, but that it has become harder to forecast.
Traditional cyber risk models depend on historical patterns, known threat actors, and relatively stable motivations. Geopolitics disrupts these assumptions. Elections, armed conflicts, sanctions, and trade disputes can rapidly change attacker priorities and targets.
This challenge is compounded as AI increasingly powers offensive cyber operations, accelerating reconnaissance, social engineering, and intrusion campaigns. As explored in Impacts of AI on Cybersecurity (https://thereviewhive.blog/impacts-of-ai-on-cybersecurity/), automation and scale are making politically motivated attacks faster, more adaptive, and harder to attribute.
WEF focus group participants warned that cyber operations are no longer limited to espionage or retaliation. They are increasingly used to influence political outcomes, disrupt trade, and shape public perception. This makes cyber risk less linear and more volatile, demanding continuous reassessment rather than static controls.
Cyber Operations as Tools of State Power
The report draws a clear connection between cyber activity and modern statecraft. Cyber operations now sit alongside tariffs, export controls, and sanctions as instruments of geopolitical leverage.
Rather than causing immediate destruction, many state-sponsored intrusions aim for persistence. Long-term access to telecommunications networks, cloud environments, or logistics systems allows actors to monitor activity, collect intelligence, and disrupt operations at moments of strategic advantage.
Focus group participants expressed particular concern about advanced cyber operations targeting telecommunications infrastructure in the United States. These incidents highlight how commercial systems increasingly overlap with national security interests, blurring the line between corporate cyber risk and geopolitical confrontation.
At the same time, cyber-enabled fraud is increasingly used as a destabilizing force. What was once seen primarily as financial crime now intersects with influence operations and geopolitical pressure. This growing overlap is examined in depth in Cyber-Enabled Fraud as a Global Cyber Threat in 2026 (https://thereviewhive.blog/cyber-enabled-fraud-global-cyber-threat-2026/), which shows how fraud, phishing, and identity abuse are scaling globally alongside political instability.
Local Events, Global Consequences
Geopolitical instability rarely remains contained within borders. Cyber effects ripple across regions, sectors, and supply chains.
A large-scale power outage in the Iberian Peninsula, though not caused by a cyberattack, highlighted how disruptive a targeted cyber incident against critical infrastructure could be. In Europe, ongoing instability linked to the war in Ukraine has coincided with hybrid campaigns combining cyber activity, physical disruption, and disinformation. Airports, energy systems, and public trust have all been affected.
Beyond Europe, escalating tensions across the Indo-Pacific, the Middle East, and Africa are intensifying cyber risk exposure. Organizations operating across these regions face overlapping threats shaped by political rivalry, military conflict, and technological competition.
Trade Wars, Supply Chains, and Expanding Attack Surfaces
Geopolitics is also reshaping global technology and supply chains. Tariffs, export controls, and sanctions are forcing organizations to reconfigure vendors, logistics routes, and data-hosting arrangements.
Many companies are reshoring manufacturing or shifting to “trusted” regional partners. The challenge lies in speed. These transitions often happen faster than cybersecurity assessments can keep pace.
As highlighted in Supply Chain Cybersecurity and Global Risk (https://thereviewhive.blog/supply-chain-cybersecurity-global-risk/), rapid supplier changes frequently expand the attack surface. New vendors may lack mature security practices, while alternative logistics or data-hosting arrangements can introduce untested vulnerabilities.
The WEF report warns that cybersecurity teams must treat trade disruptions as triggers for renewed threat modeling and third-party risk reassessment, not merely as procurement or compliance issues.
Cybersecurity Budgets Under Pressure
Despite growing geopolitical risk, some organizations are reducing cybersecurity budgets.
Survey data shows that 12% of organizations in North America and 13% in Latin America and the Caribbean have cut cybersecurity spending due to geopolitical volatility. Economic uncertainty and inflationary pressure are driving difficult trade-offs, but the timing is concerning.
State-sponsored espionage, ransomware, and hybrid attacks are becoming more frequent and more sophisticated. Reducing defensive investment at this stage increases the likelihood that future incidents will have deeper and more lasting impact.
WEF experts caution that this imbalance between rising threat activity and constrained budgets will test organizational resilience, particularly during periods of geopolitical crisis.
Critical Infrastructure in the Crosshairs
Geopolitical tensions particularly expose vulnerabilities in the critical infrastructure that underpins modern society. Energy, water, transportation, and telecommunications systems are increasingly targeted because of their interconnected nature and high societal impact.
In April 2025, a Norwegian hydropower dam was breached, opening a floodgate and releasing 500 litres of water per second for four hours. Authorities described the incident as a deliberate act of sabotage. While damage was contained, the event demonstrated how cyber intrusions can translate directly into physical disruption.
Confidence in national cyber response is eroding. Thirty-one percent of survey respondents said they lack confidence in their country’s ability to respond effectively to major cyber incidents, up from 26% the previous year. Confidence varies sharply by region, revealing uneven preparedness and coordination across the globe.
Cybersecurity Enters the Sovereignty Era
Uneven confidence across regions points to a broader shift in how nations and organizations view cybersecurity. It is no longer seen purely as a technical challenge, but as a question of sovereignty and self-reliance.
Governments and enterprises are reassessing dependencies on foreign technology providers, global cloud infrastructure, and international supply chains. In Europe, municipalities and federal agencies have begun shifting toward sovereign or regionally managed cloud solutions to reduce exposure to extraterritorial control of data.
This shift reflects a deeper recalibration of trust. Organizations must now balance openness and interoperability against the need for autonomy, control, and resilience in an increasingly fragmented digital world.
Henna Virkkunen, Executive Vice-President for Tech Sovereignty, Security and Democracy at the European Commission, summed up this reality:
“As the threat landscape evolves and AI increasingly powers offensive operations in cyberspace, we must step up our work on the resilience of our critical infrastructure and connectivity. Our priority is to boost investments in cyber, invest in people to close the cyber skills gap, and deepen intelligence sharing so that we can spot and address vulnerabilities faster.”
Her statement reflects a growing consensus that cybersecurity has become inseparable from economic security, democratic stability, and geopolitical alignment.
What This Means for Organizations
Geopolitics is no longer an external factor to be monitored occasionally. It is a permanent input into cybersecurity strategy, board-level decision-making, and risk governance.
Organizations that are better positioned for this reality tend to invest in geopolitical threat intelligence, participate in information-sharing ecosystems, reassess vendors during trade disruptions, and prioritize resilience even under budget pressure.
Cyber risk in 2026 is shaped as much by global power shifts as by malware or vulnerabilities. Accepting that reality is now a baseline requirement for operating in the digital economy.
FAQs
Why is geopolitics so important to cybersecurity today?
Because cyber operations are increasingly used to influence political outcomes, disrupt trade, and weaken adversaries without direct military action.
Are large organizations more exposed to geopolitical cyber risk?
Yes. Global operations, complex supply chains, and regulatory fragmentation increase exposure to politically motivated cyber activity.
Why is threat intelligence becoming central to cyber strategy?
Geopolitical threats change quickly. Intelligence sharing helps organizations anticipate and adapt to shifts driven by global events.
How do trade wars increase cyber risk?
Rapid supplier and technology changes often outpace cyber due diligence, expanding third-party and supply chain vulnerabilities.
What does cyber sovereignty mean for organizations?
It reflects efforts to maintain control over data, infrastructure, and digital assets amid geopolitical uncertainty and fragmented global ecosystems.