Critical Exim Mali Server Vulnerability Impacts 1.5 Million Email Servers
Share

Security researchers have identified a critical Exim Mali Server vulnerability that currently affects more than 1.5 million email servers. This vulnerability, tracked as CVE-2024-39929, has a severity rating of 9.1 out of 10, highlighting its significant risk. It allows threat actors to bypass security protections and deliver executable attachments to user accounts, posing a severe threat to system integrity.
Exim, a free mail transfer agent, is widely used on Unix and Unix-like operating systems. Originally released in 1995 for use at the University of Cambridge, it has since become a staple in email server configurations. The identified vulnerability affects all versions of Exim up to and including 4.97.1. It arises from an error in parsing multiline headers as specified in RFC 2231, enabling attackers to bypass extension-blocking mechanisms and potentially deliver malicious executable attachments.
Heiko Schlittermann, a member of the Exim project team, confirmed the severity of the issue, stating, “I can confirm this bug. It looks like a serious security issue to me.” A recent analysis by security firm Censys revealed that out of the 6.5 million public-facing SMTP email servers, approximately 4.8 million (74%) run Exim. Among these, over 1.5 million are operating vulnerable versions, making them susceptible to potential attacks.
Historical Context and Risks
While there are no known reports of active exploitation of CVE-2024-39929, the ease of attack and the large number of vulnerable servers suggest that exploitation is imminent. This situation is reminiscent of the 2019 incident where the Kremlin-backed hacking group Sandworm exploited a severe Exim vulnerability (CVE-2019-10149) to execute malicious code with root system rights. Those attacks began two months after the vulnerability was disclosed and continued for nearly a year.
Release Candidate 3 of Exim 4.98 includes a fix for CVE-2024-39929. Administrators are strongly advised to update their systems to this latest version to mitigate the risk of exploitation. Despite the need for end users to click on an attached executable for the attack to succeed, the risk remains high due to the effectiveness of social engineering tactics commonly employed by attackers.
Steps to Quickly Patch
- Identify the Vulnerability
Understand the specific vulnerability affecting your system. For Exim servers, the current critical vulnerability is tracked as CVE-2024-39929.
- Download the Patch
Obtain the latest patch from the official Exim website or repository. For CVE-2024-39929, the fix is available in the Release Candidate 3 of Exim 4.98.
- Backup Your System
Before applying any patches, ensure you have a complete backup of your server. This step is crucial to prevent data loss in case something goes wrong during the patching process.
- Apply the Patch
Use the following steps to apply the patch:
For Linux-based Systems:
- SSH into Your Server:
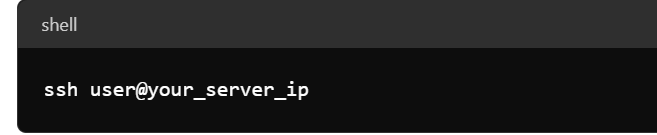
- Update Package Lists

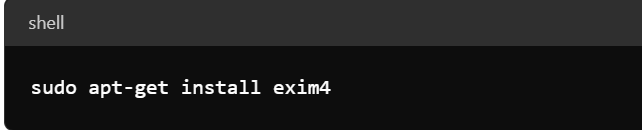
- Install the Latest Exim Version
- Verify the Installation

- Ensure the version displayed is 4.98 or later.
Check Exim Service Status

Administrators should prioritize updating their Exim installations to the latest version to protect against this and other vulnerabilities. Proactive patch management is crucial in mitigating potential threats and ensuring the security and integrity of email servers.


