Common Cyber Threats and How to Avoid Them
Share

Every minute, a cyberattack takes place somewhere in the world. That single moment can lead to financial loss, stolen personal data, erased memories, or the shutdown of essential business systems. Cyber threats are no longer distant or abstract risks. They affect everyday users, employees, small businesses, and large organizations alike. From fake emails that look genuine to malicious software running quietly in the background, cyber risks are woven into daily digital life. What makes them harder to manage is that these threats do not come from one single source. They originate from a wide mix of external attackers and internal weaknesses. Understanding how these threats work is the first step toward staying safe. This article explains the most common cyber threats in simple terms and outlines practical ways to reduce your risk.
TL;DR
Cyber threats are part of everyday digital life. Most attacks succeed not because of advanced hacking, but because of human error. Phishing, social engineering, and poor cyber hygiene remain the biggest risks. Staying alert, verifying requests, using strong passwords, enabling multi-factor authentication, and keeping systems updated can significantly reduce your exposure to cyberattacks.
Common Forms of Cyber Threats
Cyber threats are driven by different actors, each with their own motives. Knowing who is behind an attack helps explain why certain tactics are used.
- Nation-states
Governments may launch cyberattacks against rival countries to disrupt communication systems, steal sensitive data, or weaken critical infrastructure. These attacks often target utilities, financial systems, healthcare, and government institutions. While individuals may not be the direct target, they can still feel the impact through service outages or large-scale data breaches. - Terrorist organizations
Some terrorist groups use cyberattacks to create fear, damage infrastructure, and destabilize economies. Their focus is often on disruption rather than direct financial gain. - Criminal groups
Organized cybercrime groups are among the most common threats today. Their goal is financial profit. They use phishing, ransomware, spyware, and fraud to steal data, lock systems, and extort victims. These groups constantly adapt their techniques to bypass defenses. - Individual hackers
Not all attackers belong to organized groups. Some act alone, driven by personal profit, revenge, curiosity, or ideology. They often target weak passwords, outdated software, or poorly secured systems. - Malicious insiders
Insiders already have access to systems, making them especially dangerous. This could be an employee, contractor, vendor, or partner misusing their access. In some cases, attackers steal credentials and operate while appearing legitimate.
Social Engineering Attacks
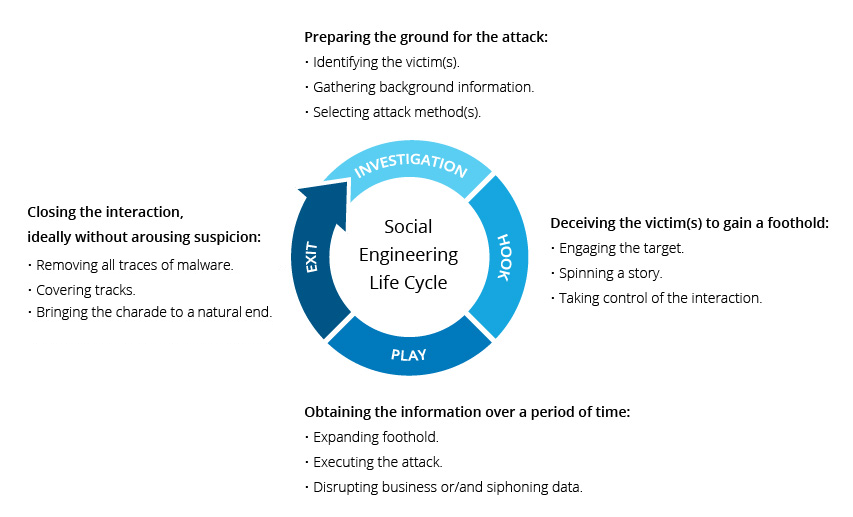 Social engineering attacks focus on manipulating people instead of exploiting technical vulnerabilities.
Social engineering attacks focus on manipulating people instead of exploiting technical vulnerabilities.
Attackers pose as trusted entities such as banks, IT support teams, delivery services, or government agencies. They contact victims through emails, phone calls, texts, or messaging apps. These messages are designed to trigger fear, urgency, or trust.
Social engineering often unfolds in stages. Attackers first gather background information, such as job roles, company processes, or online behavior. They then craft believable messages that push victims into acting quickly.
What makes social engineering especially dangerous is its reliance on human error. Unlike software vulnerabilities, human behavior cannot be patched, which makes these attacks harder to detect and prevent.
Common Social Engineering Attack Methods
- Phishing
Phishing remains one of the most common cyber threats. Attackers send messages that appear to come from legitimate organizations. These messages often contain urgent warnings or tempting offers. Clicking the link can lead to fake login pages or malware installation. - Baiting
Baiting attacks rely on temptation. Victims may be offered free downloads, prizes, or physical items like USB drives labeled as confidential. Once accessed, malware is installed on the system. - Pretexting
In pretexting, attackers create a false scenario to gain trust. They may impersonate law enforcement, IT staff, or financial institutions to convince victims to share sensitive information.
Effective Cyber Hygiene: Essential Ways to Safeguard Yourself
 1. Be Cautious About Manipulation
1. Be Cautious About Manipulation
- Attackers often exploit emotions. Messages that create panic or excitement should raise suspicion. Pause before reacting to threats of fines, account suspension, or unexpected rewards.
- Always verify identities. Contact organizations using official details from their website, not the information provided in the message.
- Be wary of strangers who attempt to build instant trust or request sensitive information without proper verification.
2. Think Before You Click
Many attacks succeed only because a user clicks a link or opens an attachment.
- Avoid suspicious links and downloads. Offers that sound unrealistic usually are.
- Never insert unknown USB devices into your computer.
- Do not share passwords or one-time codes through email or messages.
3. Use a Strong Security Setup
- Prepare for human error through awareness and training.
- Monitor access and permissions within organizations.
- Use firewalls and secure networks and treat public Wi-Fi as unsafe.
- Enable multi-factor authentication on all critical accounts.
- Use strong, unique passwords and consider a password manager.
- Keep operating systems, apps, and browsers updated.
- Use reliable antivirus and anti-malware tools and keep them current.
To Sum Up
Cyber threats are a constant reality in today’s connected world. They come from many sources and rely heavily on human mistakes rather than advanced technology alone.
You don’t need to be a cybersecurity expert to stay safer online. Awareness, caution, and basic security practices can significantly reduce your risk. Every secure habit, no matter how small, adds another layer of protection.
Cybersecurity begins with informed choices; made one click at a time.
FAQs
What is the most common cyber threat today?
Phishing remains the most common cyber threat. Attackers rely on fake emails, messages, and websites to trick users into sharing credentials or installing malware.
Why are social engineering attacks so effective?
They exploit human emotions like fear and urgency. Since they rely on human behavior rather than software flaws, they are harder to detect and prevent.
Can antivirus software alone protect me from cyber threats?
No. Antivirus software helps, but it cannot prevent attacks that rely on user actions, such as phishing or social engineering. Awareness and good habits are just as important.
Is multi-factor authentication really necessary?
Yes. MFA adds a critical layer of security. Even if your password is compromised, MFA can prevent unauthorized access.
How often should software updates be installed?
Updates should be installed as soon as they are available. Delayed updates leave known vulnerabilities open to attackers.

