Trello API Breach: 15 Million Email Addresses Leaked on Hacking Forum
Share

A significant Trello API data breach has exposed over 15 million email addresses associated with Trello accounts, leaking them on a hacking forum. This incident, traced back to an unsecured API in January, has heightened concerns regarding data security and privacy, particularly for businesses relying on Trello for project management.
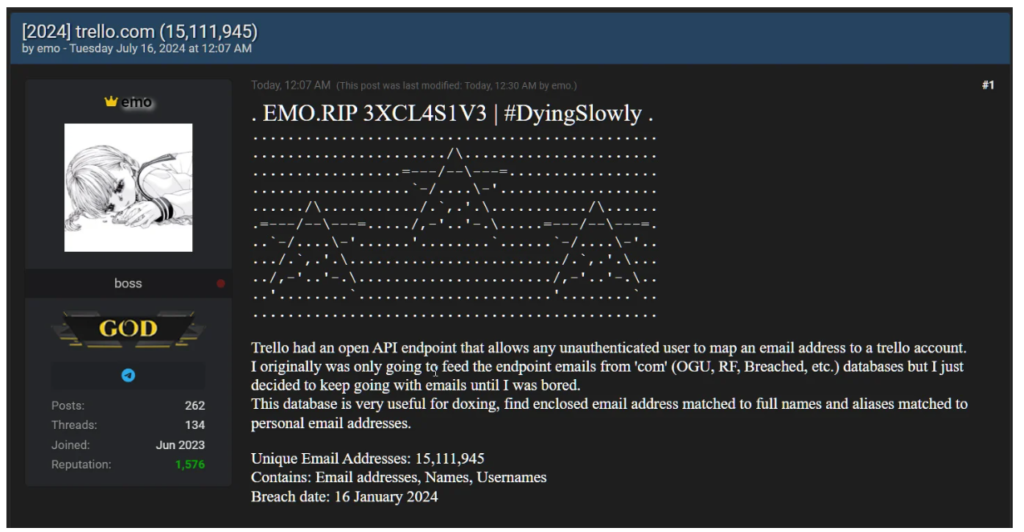
Trello, owned by Atlassian, is a popular online project management tool widely used to organize data and tasks into boards, cards, and lists. In January, BleepingComputer reported that a threat actor known as ’emo’ was selling profiles for 15,115,516 Trello members on a well-known hacking forum. Despite most of the data in these profiles being public information, each profile contained a non-public email address linked to the respective account.
While Atlassian, the owner of Trello, did not initially confirm the method of data theft, emo revealed that the data was collected using an unsecured REST API. This API allowed developers to query public profile information based on users’ Trello ID, username, or email address. Emo created a list of 500 million email addresses and fed them into the API to determine if they were linked to a Trello account. The returned account information was then used to create member profiles for over 15 million users.
Source: BleepingComputer
Emo has shared the entire list of 15,115,516 profiles on the Breached hacking forum for eight site credits, worth $2.32. “Trello had an open API endpoint that allowed any unauthenticated user to map an email address to a Trello account,” emo explained in the forum post. “I originally planned to use emails from ‘com’ databases but continued until I was bored.”
The leaked data includes email addresses and public Trello account information, including users’ full names. This information can facilitate targeted phishing attacks to steal more sensitive data, such as passwords. Emo also mentioned that the data could be used for doxxing, enabling threat actors to link email addresses to people and their aliases.
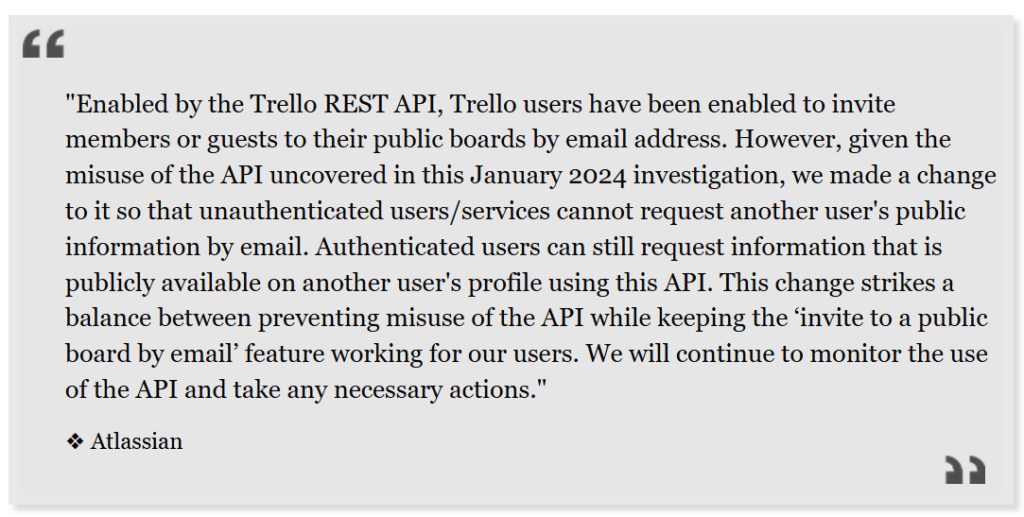
Atlassian confirmed to BleepingComputer today that the information was indeed collected through a Trello REST API, which was secured in January. However, this Trello API data breach highlights the ongoing risks posed by unsecured APIs.
Unsecured APIs have become a popular target for threat actors, who exploit them to combine non-public information, such as email addresses and phone numbers, with public profiles. In 2021, threat actors used an API to link phone numbers to Facebook accounts, creating profiles for 533 million users. Similarly, in 2022, Twitter suffered a breach where threat actors linked phone numbers and email addresses to millions of users via an unsecured API.
More recently, an unsecured Twilio API was used to confirm the phone numbers of 33 million Authy multi-factor authentication app users. Many organizations try to secure APIs using rate-limiting rather than through authentication via an API key. However, threat actors circumvent these measures by purchasing hundreds of proxy servers and rotating connections to continuously query the API, rendering rate-limiting ineffective.
The Trello API data breach serves as a stark reminder of the critical importance of securing APIs to protect user data and maintain privacy. In today’s digital landscape, the vulnerability of APIs has become a major concern. As businesses increasingly rely on APIs to connect services and share data, the potential for misuse by threat actors grows.
To mitigate such risks, organizations must prioritize API security by implementing robust authentication methods, such as API keys, OAuth, and token-based authentication. Additionally, employing encryption to protect data transmitted via APIs can prevent unauthorized access. Regularly updating and patching APIs to address vulnerabilities is also essential in maintaining security.
Furthermore, businesses should consider using API gateways to manage and monitor API traffic. API gateways can provide additional security features, such as rate limiting, IP whitelisting, and anomaly detection, to safeguard against abuse. Conducting regular security audits and penetration testing can help identify and address potential weaknesses in API implementations.
Educating employees and users about the risks associated with unsecured APIs and the importance of protecting sensitive information is equally important. By fostering a culture of security awareness, organizations can better defend against potential breaches and ensure the safety of their data.
The Trello API data breach underscores the need for businesses to remain vigilant in their cybersecurity efforts. As threat actors continue to exploit vulnerabilities in APIs, it is crucial for organizations to stay ahead of potential risks and implement comprehensive security measures. By doing so, they can protect their data, maintain user trust, and avoid the damaging consequences of data breaches.
In conclusion, the Trello API data breach, which exposed the email addresses of over 15 million users, highlights the critical importance of securing APIs. As businesses and individuals increasingly rely on APIs to connect services and share information, the potential for misuse by threat actors grows. Organizations must prioritize API security by implementing robust authentication methods, encryption, and regular updates, as well as utilizing API gateways and conducting security audits. By taking these steps, businesses can protect their data, maintain user trust, and prevent future breaches.










