Shadow AI and Cyber Risks: The Hidden Threat Inside Enterprises
Share
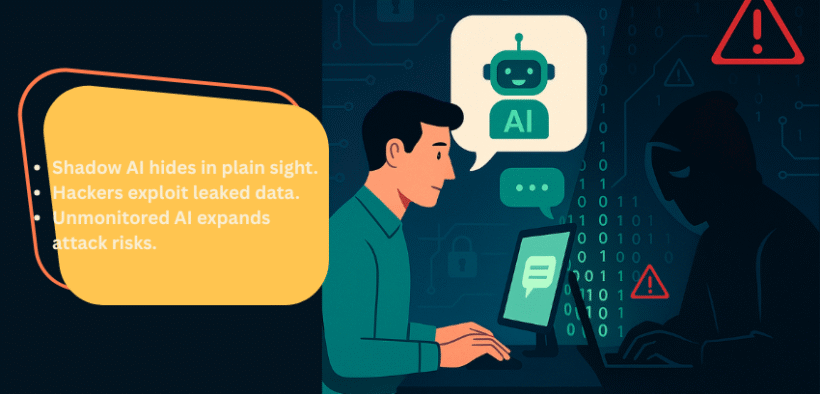
Shadow AI and cyber risks have quickly become one of the most pressing challenges for modern enterprises. Shadow AI refers to the unsanctioned use of artificial intelligence tools by employees without the knowledge or approval of IT and security teams. What began as harmless experimentation—using ChatGPT to polish an email or Copilot to suggest a line of code—has evolved into a serious security blind spot.
Surveys reveal that more than half of employees already use AI tools without approval, with nearly 90% admitting they’ve entered work-related data into these systems, and around 40% confessing that the information was confidential. This hidden usage bypasses organizational safeguards, introduces compliance risks, and creates attack surfaces that remain invisible to traditional monitoring.
The risks are no longer theoretical. From leaked source code at Samsung to the Pentagon banning the Chinese AI tool DeepSeek, real-world cases prove that shadow AI is already impacting businesses and governments alike. Unlike traditional shadow IT, shadow AI doesn’t just store or transfer data; it processes and learns from it, making any exposure potentially permanent. For cybersecurity teams, this creates a new category of threats where data leakage, unmonitored workflows, and AI-powered phishing converge. Shadow AI is no longer just a governance problem—it’s a frontline cyber risk with real financial, reputational, and even national security consequences.
TL;DR
- Shadow AI = new attack vector. Employees secretly using AI tools create invisible entry points for cybercriminals.
- Data exposure is widespread. Around 90% of workers have entered work data into AI tools, and nearly 40% admit that data was confidential.
- Breach costs rise. Organizations with uncontrolled AI use face higher breach costs and more severe compliance penalties.
- Attackers adapt fast. Threat actors exploit shadow AI practices to harvest data and automate phishing or malware.
- Defenses exist. Monitoring, AI firewalls, governance, and staff training reduce cyber risks while keeping innovation alive.
Key Points:
- Over half of employees worldwide use unsanctioned AI tools, with many hiding it from managers.
- Nearly 90% of workers have entered work-related data into AI tools; 38–40% say that data was confidential.
About 80% of IT leaders have reported negative outcomes from shadow AI, including financial and reputational harm. - Developers relying on AI assistants risk introducing insecure code, which attackers actively exploit.
- Real-world cases like Samsung’s code leak and the Pentagon’s DeepSeek ban highlight how quickly shadow AI can escalate into cyber risks.
Why Shadow AI Fuels Cybersecurity Risks
1. Data Leakage Becomes Inevitable
When employees paste sensitive code, contracts, or customer records into AI prompts, that data leaves the company perimeter. Even if providers claim not to train on it, it’s still processed externally—where organizations lose control. For hackers, this is a treasure chest of exposed data waiting to be discovered.
2. Invisible Attack Surfaces
Traditional security tools monitor known apps and systems. Shadow AI bypasses this visibility. With nearly 90% of AI usage invisible to IT teams, attackers can exploit unmonitored channels to steal or manipulate data without triggering alerts.
3. Compliance Gaps Lead to Exploitable Weaknesses
Regulations like GDPR, HIPAA, and PCI DSS impose strict data handling rules. Shadow AI bypasses these controls. Hackers know that organizations often fail audits when employees use unapproved tools, making them softer targets for ransomware or extortion.
4. AI-Generated Code Vulnerabilities
Developers using unsanctioned AI coding assistants risk embedding insecure or unverified code into production. Cybercriminals actively scan for these vulnerabilities, turning poorly reviewed AI-generated snippets into exploitable backdoors.
5. Phishing and Social Engineering Amplified
Shadow AI isn’t just a victim risk—it’s also a tool for attackers. When employees normalize secret AI use, adversaries slip in with lookalike “free AI tools” or malicious browser extensions. These harvest credentials, monitor activity, and even craft spear-phishing campaigns automatically.
Real-World Cyber Incidents Involving Shadow AI
- Samsung Case: Employees pasted sensitive source code into ChatGPT. This created a risk that proprietary algorithms could be exposed outside the company.
- Pentagon DeepSeek Ban: The U.S. Department of Defense banned the use of DeepSeek, a Chinese AI platform, citing risks that sensitive government data could be accessed by foreign entities.
- Scale AI Leak: A major data-labeling firm accidentally exposed sensitive client information, including projects with Meta and xAI, through poorly controlled document sharing. While not a direct AI misuse, it highlighted how loosely managed AI workflows can leak confidential data.
- Industry Trends: IBM’s 2025 breach report confirmed that shadow AI practices increase the cost of data breaches, with organizations facing extended containment times and heavier compliance fines.
- Free AI Tool Risks: Surveys show that a majority of employees use free AI platforms at work, with about 65% relying on free tiers that may store or train on entered data—an open door for cyber risks.
Shadow AI as a Cyber Threat Multiplier
Shadow AI doesn’t just create isolated risks—it intensifies existing cybersecurity challenges, making them harder to detect, manage, and contain. Let’s have a look at how.
Insider Threats
Employees who secretly use AI tools can unintentionally—or intentionally—exfiltrate sensitive data. Unlike traditional insider risks, shadow AI gives them an easy cover. Copying entire datasets into a prompt looks like simple “usage,” not malicious activity, which makes it harder for monitoring tools to flag. In some cases, employees may not even realize that what they’ve shared is harmful until it’s too late. This makes shadow AI a powerful enabler of both accidental and deliberate insider threats.
Supply Chain Attacks
Unapproved AI tools often connect to external APIs, third-party plug-ins, and cloud services. Each of these integrations adds another layer to the organization’s attack surface. Hackers can exploit weaknesses in those external connections to infiltrate enterprise networks. Because IT has no visibility into these shadow connections, supply chain risks multiply. A single hidden integration can open the door to data theft or malware injection, bypassing otherwise strong defenses.
Shadow Malware Delivery
Cybercriminals have begun disguising malware as “AI helpers” or free AI extensions. Employees looking for productivity shortcuts might install them without IT approval. These tools may appear legitimate but are designed to harvest credentials, monitor keystrokes, or establish backdoors. Because they’re framed as “AI tools,” they may escape traditional malware detection and blend into normal activity. This creates a new delivery mechanism for attackers to compromise enterprise systems.
Advanced Social Engineering
Generative AI allows attackers to craft highly convincing phishing campaigns, deepfake communications, or spoofed identities at scale. Shadow AI habits make this worse: when employees normalize secret AI use, they’re more likely to trust or fall for “AI-enabled” phishing lures. Attackers can mimic executives’ voices, generate flawless spear-phishing emails, or create fake chatbots that employees assume are legitimate. In essence, shadow AI lowers defenses while attackers raise the sophistication of their tricks.
Shadow AI Risk Matrix: From Risk to Defense
|
Shadow AI Risk |
Cybersecurity Impact |
Mitigation Strategy |
|
Data Leakage |
Confidential data (source code, contracts, PII) leaves company control and may be exposed permanently. |
Deploy AI firewalls and DLP tools to block sensitive prompts before leaving the network. |
|
Insider Threats |
Employees exfiltrate or mishandle data under the guise of “AI usage,” harder to detect. |
Monitor AI traffic, enforce least-privilege access, and create clear usage policies. |
|
Supply Chain Expansion |
Unapproved AI APIs and plug-ins create hidden integration points attackers can exploit. |
Vet all third-party AI tools, maintain an AI vendor risk management program. |
|
Shadow Malware Delivery |
Fake “AI helper” apps install trojans, steal credentials, or open backdoors. |
Educate staff on risks, restrict installations, and use endpoint detection solutions. |
|
AI-Generated Code Flaws |
Insecure or vulnerable code introduced into production environments. |
Mandate secure code reviews, scanning, and continuous testing of AI-generated code. |
|
Compliance Violations |
Breach of GDPR, HIPAA, PCI DSS, or industry regulations from unsanctioned data use. |
Define approved tools, enforce data policies, and maintain regular compliance audits. |
|
Advanced Social Engineering |
AI-enabled phishing, deepfakes, or spoofed communications trick employees. |
Provide awareness training, deploy email security gateways, and verify communications. |
6 Ways to Defend Against Shadow AI Cyber Risks
1. Discover and Monitor AI Traffic
The first step in defending against shadow AI is visibility. You can’t protect what you can’t see. Most organizations underestimate how much AI activity flows through their networks because employees access AI tools from personal devices or web browsers. Deploying monitoring solutions that specifically recognize AI-related traffic—such as prompts sent to ChatGPT or API calls to Copilot—can uncover hidden usage. Integrating Data Loss Prevention (DLP) systems or SaaS discovery platforms gives IT teams real-time insight into who is using AI, what data is being shared, and whether it violates policy. Without this visibility, sensitive information may already be leaving your systems unnoticed.
2. Deploy AI Firewalls and Data Filters
AI firewalls are emerging as a critical defense against shadow AI risks. These tools sit between users and external AI platforms, scanning prompts before they are sent out. Sensitive information such as source code, personal data, or financial records can be redacted automatically. This reduces the chance of accidental data leakage even when employees attempt to use external AI systems. Think of it as a smart checkpoint: employees can still benefit from AI assistance, but only after dangerous data is filtered out. This approach also ensures that compliance requirements are met, since no unapproved data crosses organizational boundaries.
3. Harden Developer Practices
Developers are among the heaviest users of shadow AI. Tools like GitHub Copilot or ChatGPT can generate code quickly, but that code isn’t always secure. Vulnerabilities, weak encryption, or inefficient practices may be introduced without developers realizing it. To counter this, organizations must enforce secure development practices such as mandatory code reviews, static analysis scans, and penetration testing. AI-generated code should never bypass the same scrutiny applied to human-written code. By setting this standard, companies can enjoy the productivity boost of AI coding tools without increasing their exposure to exploitable weaknesses.
4. Policy and Governance First
Technology alone can’t solve shadow AI. Clear policies are essential. These should outline which AI tools are approved, what kinds of data employees can use, and how risks will be managed. Policies must go beyond simply “do not use AI.” Instead, they should guide employees with practical rules such as “customer PII cannot be entered into external AI” or “use only the enterprise-licensed version of Copilot.” Governance frameworks should also assign responsibility—who in the organization owns AI oversight, how often reviews take place, and what happens when violations occur. A strong policy gives employees confidence that they are using AI responsibly, while protecting the organization from hidden risks.
5. Awareness Training
Employees are often unaware that their AI use poses risks. Many see AI tools as harmless helpers, not realizing that prompts may leave the company’s control. Training programs should highlight real-world incidents, such as the Samsung case where employees pasted source code into ChatGPT. By grounding awareness in true examples, training makes the risks relatable. It should also teach employees how to use AI securely—what to share, what to avoid, and how to report suspicious tools. Awareness is not about scaring employees but about empowering them to make safer decisions. A workforce that understands shadow AI risks is the first line of defense against them.
6. Incident Response Planning
Even with monitoring, policies, and training, shadow AI incidents will happen. That’s why a response plan is critical. Organizations need playbooks that specifically address shadow AI scenarios, such as when an employee uploads confidential data into an unauthorized platform. The plan should cover containment steps (e.g., revoking access, isolating affected accounts), forensic analysis (understanding what data was shared and how far it spread), and remediation (reporting to regulators if required, tightening controls, and retraining staff). By preparing for the worst, companies can reduce damage, recover quickly, and demonstrate compliance to auditors and regulators.
FAQs
Q1. How does shadow AI increase cyber risks?
By creating invisible data flows, exposing sensitive information, introducing insecure code, and bypassing compliance safeguards.
Q2. Can shadow AI be exploited by hackers?
Yes. Attackers can set up fake AI tools, intercept data, or exploit AI-generated vulnerabilities.
Q3. Is shadow AI a bigger risk than shadow IT?
Yes. Shadow IT involves apps or devices, but shadow AI processes and learns from data. This creates permanent risks once sensitive information is exposed.
Q4. How can businesses reduce shadow AI threats?
Through monitoring, governance, employee training, and safe alternatives like vetted enterprise AI tools.
To Sum Up
Shadow AI is no longer just an IT governance problem—it’s a cybersecurity threat. By hiding AI use, employees unknowingly create new attack surfaces for hackers. Real cases like Samsung’s code leak or the Pentagon’s DeepSeek ban prove how dangerous shadow AI can be. The answer isn’t to ban AI outright, but to see it, govern it, and secure it. With proper visibility, policies, and safe AI options, organizations can harness AI’s power while reducing the cyber risks it brings. Companies that understand the link between shadow AI and cybersecurity today will be far better prepared for the threats of tomorrow.