Phishing Attacks Employing QR Codes
Share
Background
In the ever-evolving landscape of cyber threats, phishing attacks continue to be a major threat for individuals and organizations alike. These attacks have evolved over the years, incorporating new techniques to lure victims into disclosing sensitive information or downloading malicious software. One such evolving technique is the use of QR codes in phishing campaigns. QR codes, originally designed for convenience and efficiency, have now become a tool of choice for cybercriminals. In this blog, we will examine phishing attacks employing QR codes, exploring their mechanisms, common tactics, and mitigation strategies.
Understanding QR Codes
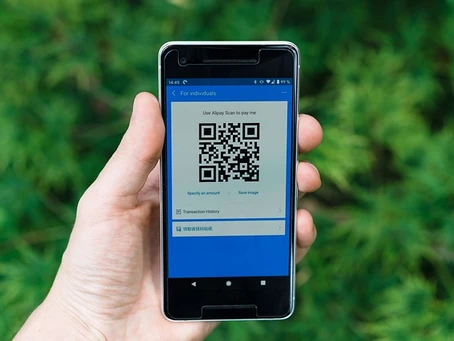
QR codes, short for Quick Response codes, were created in Japan in the 1990s as a means to quickly decode information. These two-dimensional barcodes store data, such as URLs, text, or contact information, and can be easily scanned by smartphones and other QR code readers. Their convenience and efficiency have made QR codes ubiquitous in various industries, from marketing and advertising to ticketing and payment systems.
However, this same convenience that makes QR codes popular for legitimate purposes has also made them an attractive tool for cybercriminals. Phishers have recognized the potential of QR codes as a new avenue to trick victims into revealing sensitive information or infecting their devices with malware.
How Phishing with QR Codes Works
Phishing attacks employing QR codes follow a simple yet effective modus operandi:
Creation of Malicious QR Code:
Cybercriminals create QR codes that link to malicious websites, fake login pages, or malware-infected apps. These QR codes are often disguised to appear legitimate, making them difficult for users to discern as threats.
Distribution:
Phishers distribute these QR codes through various channels, such as email, social media, printed materials, or even physical stickers placed in public places. They may use enticing messages or offers to encourage users to scan the QR code.
Scanning the QR Code:
When a user scans the malicious QR code with their smartphone or QR code reader, they are directed to a deceptive website or app that mimics a trusted service or organization. For instance, it could impersonate a banking login page or a popular e-commerce site.
Information Capture:
Victims are prompted to enter their sensitive information, such as login credentials, credit card details, or personal identification numbers (PINs), into the fake website or app. In the next step, the attackers capture this information.
Payload Delivery:
In some cases, the malicious QR code may also deliver malware onto the user’s device, compromising its security and potentially leading to further data theft or control by the attacker.
Common Tactics in QR Code Phishing
Phishers employ a variety of tactics to make their QR code phishing campaigns more convincing and successful:
Branding and Logo Mimicry:
Attackers often replicate the logos and branding of well-known companies or organizations to make their fake websites or apps appear authentic. This creates a sense of trust, luring users into divulging their information.
Urgency and Scare Tactics:
Phishers may use urgency or scare tactics to pressure victims into taking immediate action. For example, they might claim that an account will be locked unless the user verifies their credentials.
Redirects:
Some QR code phishing attacks involve multiple redirections. Victims are initially directed to a benign-looking page, which then redirects them to the malicious site. This can make it more challenging to detect the scam.
Social Engineering:
Attackers leverage psychological manipulation techniques to exploit human trust. They may use personalization, empathy, or other emotional triggers to increase the chances of success.
Exploiting Current Events:
Cybercriminals often take advantage of trending topics or current events to craft QR code phishing campaigns. For example, during a global health crisis, they may distribute QR codes promising access to COVID-19 information or resources.
Mitigating QR Code Phishing Attacks
Protecting yourself or your organization from QR code phishing attacks requires a combination of vigilance, education, and technology:
Education and Awareness:
Ensure that employees, family members, and colleagues are educated about the risks associated with QR codes. Encourage them to be cautious when scanning QR codes from untrusted sources or suspicious-looking materials.
QR Code Scanner App:
Use a reputable and secure QR code scanner app on your smartphone. These apps often come with built-in security features that can help detect and alert you to potentially malicious QR codes.
Check the URL:
Before entering any sensitive information, check the URL of the website or app that the QR code leads to. Ensure that it matches the legitimate website’s URL and is secured with HTTPS.
Two-Factor Authentication (2FA):
Enable 2FA wherever possible, especially for critical accounts like email, banking, and social media. This step adds an extra layer of security, making it harder for cyber attackers to compromise your accounts.
Regular Software Updates:
Keep your smartphone and QR code reader app updated with the latest security patches and updates. This helps protect against known vulnerabilities.
Report Suspected Phishing:
If you come across a QR code or website that appears to be a phishing attempt, report it to the relevant authorities or organizations. Many companies have dedicated channels for reporting phishing incidents.
Security Awareness Training:
Organizations should provide regular security awareness training to employees, teaching them how to recognize phishing attempts and the risks associated with QR codes.
Final Note
Phishing attacks employing QR codes represent a growing threat in the digital domain. As technology advances, so do the tools and techniques of cybercriminals. It is imperative that we stay informed, adapt to the evolving threat landscape, and work collectively to defend against phishing attacks, including those that leverage QR codes. By doing so, we can better prevent our personal and organizational data from falling into the wrong hands.