Facebook Ads Malware Campaign Pushes Information-Stealing Threat
Share

Cybercriminals are leveraging Facebook ads to distribute fake Windows desktop themes that install SYS01, a password-stealing malware, on unsuspecting users’ computers. According to Trustwave researchers, these campaigns also promote fake downloads for pirated games, software, Sora AI, 3D image creators, and One Click Active tools.
How the Malware Campaign Works
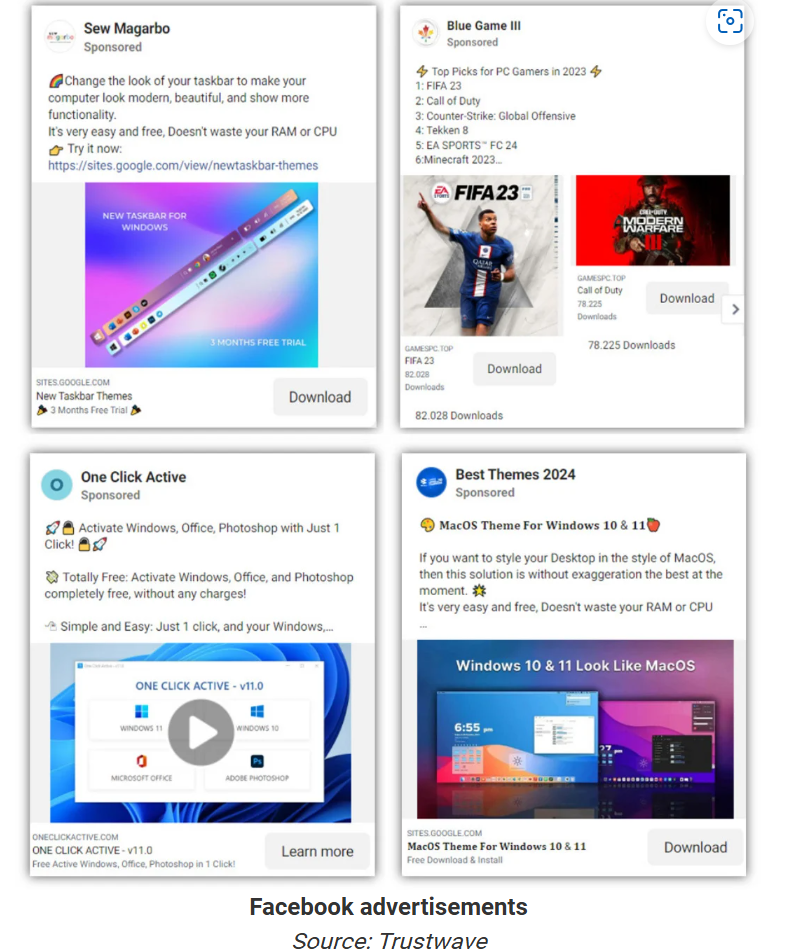 Using Facebook’s vast reach, cybercriminals create business pages and advertisements to lure users. These ads offer Windows themes, game downloads, and software cracks for popular applications like Photoshop and Microsoft Office. The threat actors either create new Facebook pages or hijack existing ones, renaming them to match the advertised content. This tactic amplifies the reach of their fraudulent ads by leveraging the follower base of the hijacked pages.
Using Facebook’s vast reach, cybercriminals create business pages and advertisements to lure users. These ads offer Windows themes, game downloads, and software cracks for popular applications like Photoshop and Microsoft Office. The threat actors either create new Facebook pages or hijack existing ones, renaming them to match the advertised content. This tactic amplifies the reach of their fraudulent ads by leveraging the follower base of the hijacked pages.
 “The threat actors assume the business identity by renaming the Facebook pages, allowing them to leverage the existing follower base to amplify the reach of their fraudulent advertisement significantly,” reads the Trustwave report. These pages have been managed by individuals in Vietnam or the Philippines at various points. Trustwave reports that each campaign involves thousands of ads, with top campaigns named blue-softs (8,100 ads), xtaskbar-themes (4,300 ads), newtaskbar-themes (2,200 ads), and awesome-themes-desktop (1,100 ads).
“The threat actors assume the business identity by renaming the Facebook pages, allowing them to leverage the existing follower base to amplify the reach of their fraudulent advertisement significantly,” reads the Trustwave report. These pages have been managed by individuals in Vietnam or the Philippines at various points. Trustwave reports that each campaign involves thousands of ads, with top campaigns named blue-softs (8,100 ads), xtaskbar-themes (4,300 ads), newtaskbar-themes (2,200 ads), and awesome-themes-desktop (1,100 ads).
From Facebook Ad Clicks to Malware Infection
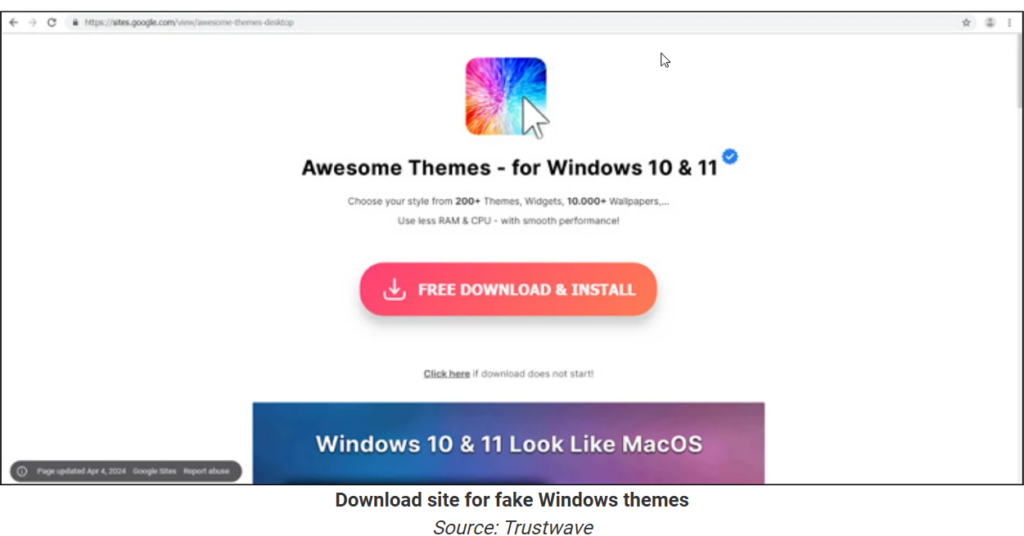
When users click on these ads, they are directed to webpages hosted on Google Sites or True Hosting. These pages pretend to offer the advertised content for download. For example, a user might see a download page for a Windows theme or Photoshop. Clicking the ‘Download’ button triggers the download of a ZIP archive named after the advertised item, such as ‘Awesome_Themes_for_Win_10_11.zip’ or ‘Adobe_Photoshop_2023.zip.’
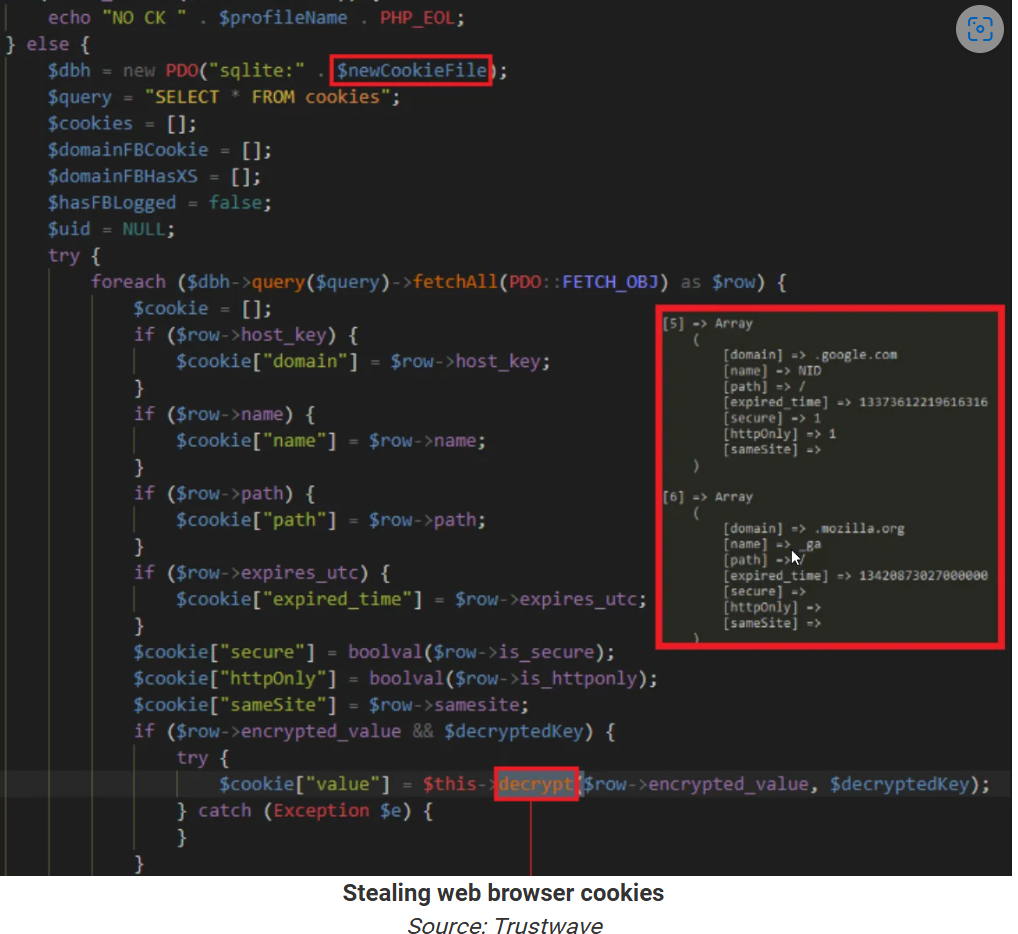 Unbeknownst to users, these ZIP files contain the SYS01 malware. Discovered by Morphisec in 2022, SYS01 uses a combination of executables, DLLs, PowerShell scripts, and PHP scripts to install itself and steal data from infected computers. When the archive’s main executable is loaded, it uses DLL sideloading to run a malicious DLL that sets up the malware’s environment. This includes:
Unbeknownst to users, these ZIP files contain the SYS01 malware. Discovered by Morphisec in 2022, SYS01 uses a combination of executables, DLLs, PowerShell scripts, and PHP scripts to install itself and steal data from infected computers. When the archive’s main executable is loaded, it uses DLL sideloading to run a malicious DLL that sets up the malware’s environment. This includes:
- Running PowerShell scripts to prevent detection by disabling virtualization environments
- Adding folder exclusions in Windows Defender
- Configuring a PHP operating environment to load malicious scripts
Impact of SYS01 Malware
SYS01 primarily steals browser cookies, saved credentials, browser history, and cryptocurrency wallets. It also exploits Facebook cookies found on infected devices to extract personal profile information, detailed advertising account data, and information about Facebook pages managed by the user.
“The ongoing SYS01 malvertisement campaign poses a threat to a wider audience and shows the importance of being aware of what users do on social media,” Trustwave concludes. The stolen data is temporarily stored in the %Temp% folder before being sent to the attackers. Stolen cookies and passwords can be sold to other cybercriminals or used to compromise additional accounts, while Facebook data is often used to hijack more accounts for future malvertising campaigns.
This type of malvertising is not confined to Facebook alone. Trustwave has observed similar profiles set up on LinkedIn and YouTube. A similar campaign was reported in February, involving the Ov3r_Stealer password-stealing malware. Recently, Bitdefender warned of threat actors hijacking Facebook pages with millions of users to impersonate popular AI projects and distribute malware like Rilide, Vidar, IceRAT, and Nova.
Preventative Measures and Awareness
The persistent threat of SYS01 and similar malware campaigns underscores the need for vigilance when interacting with online advertisements and downloading software. Users should:
- Be cautious of ads offering free downloads: If an offer seems too good to be true, it probably is. Stick to official websites and trusted sources for software downloads.
- Check the authenticity of business pages: Look for signs that a Facebook page might be hijacked, such as recent name changes or unusual activity.
- Use comprehensive security software: Anti-malware tools can help detect and block malicious downloads and prevent infections.
- Stay informed about cybersecurity threats: Regularly update your knowledge about the latest malware campaigns and tactics used by cybercriminals.
By following these guidelines, users can better protect themselves from falling victim to information-stealing malware campaigns like SYS01. Awareness and caution are key in maintaining online security and safeguarding personal information.
The Facebook ads malware campaign utilizing SYS01 is a stark reminder of the evolving tactics cybercriminals employ. By promoting fake downloads through ads and hijacked pages, they effectively spread information-stealing malware to a wide audience. Trustwave’s findings highlight the importance of being cautious online, especially when engaging with ads and downloading software. Staying informed and vigilant can significantly reduce the risk of malware infections and protect personal and financial data from being compromised.










