Apple Vision Pro Hacked: Kernel Exploit Found on Launch Day
Share
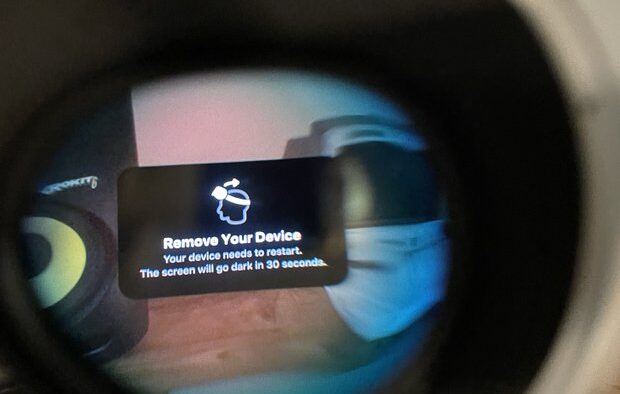
Just when the revolutionary Apple Vision Pro was settling into the hands of early adopters, a PhD student from MIT threw a wrench in the hype machine, claiming to have discovered a critical kernel exploit. Joseph Ravichandran, known for his previous research on the PACMAN attack affecting Apple M1 chips, shared his findings online, showcasing an image of the headset crashing and displaying a “remove device” warning.
This kernel exploit, targeting the core of the VisionOS operating system, poses a significant security risk. Kernel exploits are highly sought after by attackers as they grant unauthorized access, allowing for the execution of malicious code with elevated privileges and potential system takeover. Ravichandran’s demonstration highlights the vulnerability, raising concerns about the security of the highly anticipated headset, especially considering its hefty price tag.
The exploit comes on the heels of visionOS 1.0.2, released just days before the launch, aiming to patch vulnerabilities in the Safari browser engine. This update mirrored similar patches rolled out for iOS 17.3 across Apple’s device ecosystem. Despite these efforts, Ravichandran’s discovery exposes a potentially significant security gap.
Apple has yet to comment on the exploit, leaving users and security experts waiting for their response and a potential fix. With pre-orders estimated between 160,000 and 180,000 units, a widespread vulnerability could have serious implications for early adopters.
This incident underscores the ever-present battle between attackers and tech giants in securing cutting-edge technology. While the Apple Vision Pro boasts groundbreaking features, the discovery of a kernel exploit so soon after launch serves as a stark reminder that even the most anticipated devices are not immune to security threats.
Additional Information:
- It’s important to note that Ravichandran’s demonstration did not showcase the full potential of the exploit, leaving the extent of its capabilities unclear.
- While the exploit raises concerns, it’s crucial to avoid sensationalizing the issue. There’s no evidence of widespread attacks or malicious code exploiting this vulnerability yet.
- Users should stay informed and follow updates from Apple regarding potential security patches or advisories.


Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?