Corporate Data Stolen Through Compromised Cloud File-Sharing Accounts
Share

Corporate cloud file-sharing platforms are being quietly abused as data theft hubs after attackers gained access to employee accounts and exfiltrated sensitive business files. A threat actor known as Zestix is now selling this stolen data on underground forums, claiming access to internal documents from companies using ShareFile, Nextcloud, and OwnCloud.
Investigations show that these incidents did not involve direct breaches of the platforms themselves. Instead, attackers relied on valid employee credentials stolen earlier through information-stealing malware. Malware families linked to the activity include RedLine, Lumma, and Vidar, which are widely used to harvest saved browser passwords, session cookies, autofill data, crypto wallet details, and messaging app credentials.
Sample of Zestix’s offerings on underground forums. Source: Hudson Rock
These infostealers are commonly delivered through malvertising campaigns and ClickFix-style attacks, where victims are shown fake browser errors or update prompts and tricked into running malicious commands. Once installed, the malware silently collects credentials and system data, which are later reused by threat actors.
With valid credentials in hand, attackers logged into corporate cloud file-sharing accounts, particularly in environments where multi-factor authentication was not enforced. Researchers found that many of the compromised passwords had been circulating in criminal databases for years and were never rotated, allowing attackers to reuse old access without triggering alerts.
Zestix appears to operate as an initial access broker, offering either direct access to compromised cloud accounts or large volumes of stolen data. Organizations across multiple sectors are affected, including aviation, defense, healthcare, utilities, mass transit, telecommunications, legal services, real estate, and government.
In at least 15 verified cases, employee credentials stolen by infostealer malware were directly tied to unauthorized access to cloud file-sharing environments. There is no public evidence that ShareFile, Nextcloud, or OwnCloud infrastructure was compromised. The activity points to account-level abuse rather than platform vulnerabilities.
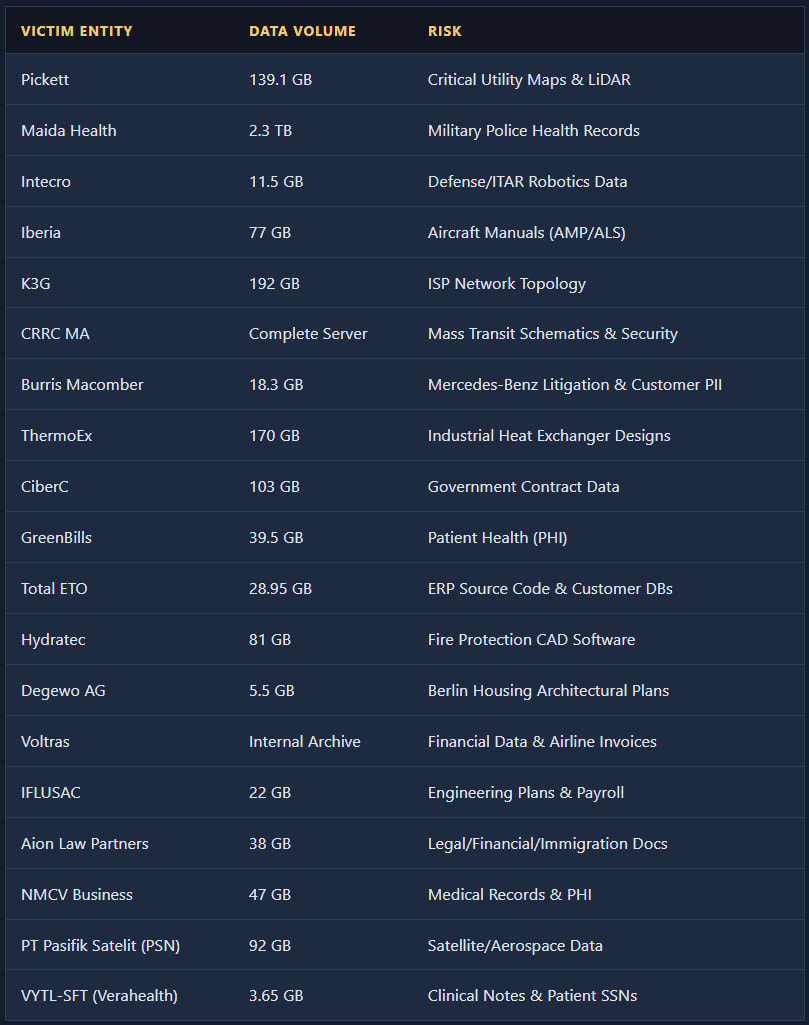
Size and type of exposed data Source: Hudson Rock
The stolen datasets being advertised range from tens of gigabytes to multiple terabytes. According to the listings, the data includes aircraft maintenance manuals, defense-related documents, medical records, transit system schematics, ISP network configurations, satellite project files, ERP source code, government contracts, and legal documentation.
Researchers also identified thousands of infected endpoints potentially linked to this activity. Some systems were associated with large enterprises, including Deloitte, KPMG, Samsung, Honeywell, and Walmart.
Affected service providers have been notified so they can investigate exposed accounts and take corrective action.


