How to Protect Yourself from QR Code Phishing
Share

QR codes, once a symbol of seamless connectivity, have become a breeding ground for a sophisticated cyber-attack known as QR code phishing, or “quishing.” The ubiquity of QR codes has witnessed a remarkable surge in recent years. Solidifying this trend, a June 2021 survey of U.S. shoppers revealed that nearly half (45%) reported using a QR code to access marketing or promotional offers. In 2022 by statista, a staggering 89 million smartphone users in the United States scanned a QR code, representing a significant 26% increase compared to 2020. Industry projections anticipate this growth trajectory to continue, with forecasts exceeding 100 million U.S. users utilizing QR code technology by 2025. However, this increased convenience presents a crucial security concern: QR code phishing, a sophisticated cybercrime tactic exploiting the trust associated with these ubiquitous squares.
QR Code Phishing on the Rise: A 2024 Statistical Analysis
A 2024 Statistical Analysis
QR codes, once a symbol of seamless connectivity, have become a breeding ground for a sophisticated cyber threat known as QR code phishing, or “quishing.” While specific statistics for 2024 might not be readily available yet, analysis of trends from 2023 paints a concerning picture:
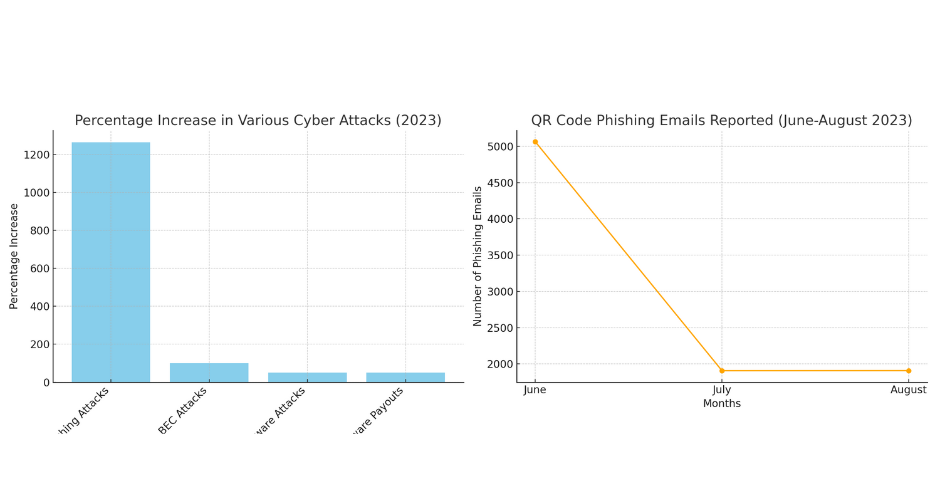
- Exponential Growth: The statistics provided by the Slashnext State of Phish reveal that there was a 1265% increase in phishing attacks in 2023. The data indicates a growing trend in deceptive practices posing risks to both individuals and organizations. Here are a few relevant statistical data by cybersecurity providers regarding various cyber-attacks.
- 100% increase in BEC attacks (Verizon DBIR)
- 51% increase in ransomware attacks on large enterprise (CrowdStrike)
- 50% increase in ransomware payouts (Chainalysis)
- QR Code Phishing Emails on the Rise: As reported by Keepnetlabs, alarming trends emerged in QR code phishing tactics between June and August 2023. Systems detected a troubling surge of 8,878 such phishing attempts between June and August, with June being the peak month at a staggering 5,063 reported cases. This data highlights the evolving strategies of cybercriminals and underscores the importance of remaining vigilant against all forms of phishing attacks, including those delivered via email.
- Widespread Threat: As per the study by Keepnetlabs, by October 2023, a significant portion (22%) of all phishing scams involved QR codes, demonstrating their growing prevalence as a tool for cybercriminals. This trend is expected to persist in 2024, as attackers exploit the increasing reliance on QR codes across various industries.
- Targeted Industries: Financial institutions, insurance companies, manufacturing giants, and technology firms are particularly susceptible to quishing attacks due to the valuable data they handle. These sectors remain high-risk targets in 2024.
- High-Value Individuals: Senior executives and managers face a higher risk of being targeted by quishing scams compared to regular employees. This trend is likely to continue in 2024, as attackers seek access to sensitive information and financial resources.
- Device Vulnerability: Over half (50%) of personal devices used by employees were targeted by phishing attempts in a single quarter during 2023. This alarming statistic underscores the need for robust security protocols on both personal and corporate devices in 2024.
- Common Tactics: Attackers primarily leverage quishing to steal usernames and passwords (89.3% of attacks). Other tactics involve deploying fake security alerts (27%) and presenting fraudulent shared documents (21%). These tactics are likely to remain prevalent in 2024.
- Global Impact: With the total number of quishing incidents exceeding 100 million, no industry or region remains unscathed. This widespread impact emphasizes the global nature of this cyber threat and the need for international collaboration in 2024.
What is QR code Phishing
QR code phishing, also known as quishing, represents a growing cyber threat that exploits the ubiquity and perceived legitimacy of QR codes. Attackers leverage these seemingly innocuous squares to target unsuspecting users and steal sensitive information or infect devices.
How do QR code scams work?
The modus operandi of QR code phishing is as follows:
- Malicious Link Embedding: Perpetrators embed fraudulent URLs within seemingly legitimate QR codes. These codes can be strategically placed on posters, flyers, product packaging, or even malicious online content.
- Deceptive Website Design: Upon scanning, the QR code redirects the user to a meticulously crafted website designed to mimic a legitimate login page for trusted institutions like banks, social media platforms, or other well-known services.
- Exploiting Security Gaps: Unlike traditional phishing emails that can be flagged by spam filters, QR code scams bypass this security layer, posing a significant threat, especially for users with a lower awareness of cybercrime tactics.
- Information Theft: Once a user interacts with the fraudulent website by entering login credentials or other sensitive data, the attacker captures this information. Stolen credentials can be used for financial gain, identity theft, or further malicious activities.
- Malware Deployment: In some instances, the QR code scam might even deploy malware onto the user’s device, compromising the entire system’s security.
What is QR code Phishing
Engaging with a compromised QR code can expose you to a variety of security threats. Here are the primary risks:
- Redirection to Phishing Sites: The most prevalent outcome is being directed to a fraudulent website designed to mimic legitimate online platforms. These websites, meticulously crafted to resemble login pages for banks, social media services, or other trusted institutions, aim to deceive you into surrendering sensitive information such as login credentials and financial details. Once entered, this information is captured by the attacker and can be used for malicious purposes, including identity theft and unauthorized financial transactions.
- Malicious Download Initiation: Phony QR codes can also be engineered to trigger downloads on your device. These downloads may contain malware, a software specifically designed to compromise your system’s security. Malware can manifest in various forms, each posing a distinct threat:
- Spyware: Covertly gathers your browsing history, login credentials, and other sensitive data.
- Ransomware: Restricts access to your device or encrypts your files, demanding a ransom payment for restoration.
- Viruses: Corrupts or deletes valuable data stored on your device.
The consequences of interacting with a malicious QR code can be severe, ranging from financial losses to identity theft and complete system compromise.
Where Do Phony Qr Codes Show Up?

QR Code in Public Place
The deceptive nature of QR code phishing necessitates heightened vigilance across various environments. Here’s a breakdown of potential locations where malicious actors might deploy phony QR codes:
Physical Environments:
- Public Infrastructure: Bus stops, lamp posts, building walls, and other public spaces where posters, flyers, or stickers displaying QR codes might be strategically placed to target unsuspecting individuals.
- Commercial Establishments: Restaurants, stores, and other businesses may utilize QR codes for menus, receipts, product packaging, or advertisements. Malicious actors may exploit this by replacing legitimate codes or placing deceptive ones directly on products, especially those susceptible to tampering.
- Unfamiliar Locations: When traveling or encountering QR codes in unfamiliar environments, it’s crucial to exercise increased caution. Lower awareness of local scams in these areas makes individuals more vulnerable.
Digital Landscape:
- Phishing Emails: QR codes embedded within emails, particularly those originating from unknown senders or emails promoting dubious offers, warrant suspicion.
- Compromised Websites: Websites with questionable content, those advertising pirated software, or promoting other illegal activities may harbor QR codes designed for malicious purposes.
- Social Media Platforms: Posts or messages containing QR codes, especially from unverified accounts or those promoting unknown products or services, should be approached with a critical eye.
Always prioritize verification before scanning.
The Multifaceted Threat of QR Code Phishing
Leveraging the growing ubiquity and perceived legitimacy of QR codes, malicious actors exploit these seemingly innocuous squares to target individuals, corporations, and data security.
Individual Threats:
- Financial Loss: Phishing websites masquerade as legitimate login pages for banks, credit cards, or online payment platforms. Once compromised, attackers can surreptitiously divert funds, execute unauthorized purchases, or even accrue debt under the victim’s identity.
- Identity Theft: Stolen personal information, such as names, addresses, Social Security numbers, or email addresses, can be weaponized for identity theft. This can lead to a cascade of problems, including fraudulent loans, manipulated tax filings, or even medical treatment billed under the stolen identity.
- Device Compromise: Malicious downloads triggered by phony QR codes can infect devices, compromising their security and functionality. Spyware can steal data, ransomware can lock users out of their files, and viruses can damage devices or corrupt data.
Corporate Financial Implications:
- Data Breaches: QR code phishing scams targeting employees can act as a Trojan horse, facilitating corporate data breaches. Stealing login credentials of authorized personnel can grant attackers access to sensitive financial information, trade secrets, or intellectual property.
- Reputational Damage: A successful phishing attack can inflict significant reputational damage on a company. Data breaches erode customer trust, and malware infections can disrupt business operations, leading to financial losses.
- Financial Fraud: Hackers can exploit stolen corporate credentials to initiate fraudulent financial transactions or divert payments into their own accounts.
Data Security Concerns:
- Loss of Sensitive Information: Phishing attacks can result in the theft of a wide range of sensitive data, including trade secrets, customer information, employee data, and intellectual property. This can have severe legal and financial repercussions for a company.
- Compliance Violations: Depending on the nature of the stolen data, a company may face hefty fines or legal action for non-compliance with data privacy regulations.
- Breach of Trust: Data breaches can severely damage a company’s relationship with its customers and partners, who entrust it with their personal information.
Signs that a QR code may be malicious or part of a scam?

Malicious QR Code
- Unfamiliar or Suspicious Sources:
QR codes from unknown or untrusted sources should be approached with caution. If you receive a QR code through unsolicited emails, social media messages, or random advertisements, especially from people or organizations you don’t recognize, it’s best to avoid scanning them. Scammers often use these methods to distribute malicious QR codes.
- Poor Quality or Altered Appearance:
A legitimate QR code should be clear and professionally printed. If a QR code appears blurry, has visible tampering like stickers placed over it, or looks altered in any way, it could be a sign that someone has replaced an original, safe QR code with a malicious one. Always inspect the quality and appearance of the QR code before scanning.
- Unexpected Requests for Personal or Financial Information:
Be wary if scanning a QR code leads to a prompt asking for sensitive information, such as passwords, credit card numbers, or personal details. Legitimate businesses typically do not request such information through QR codes. If the request seems excessive or unrelated to the context, it is likely a scam attempt.
- URLs That Do Not Match the Expected Domain:
When scanning a QR code, check the URL to ensure it matches the expected domain of the legitimate website. Scammers often use URLs that look similar but have slight variations or misspellings. Also, make sure the URL starts with “https” indicating it is secure. If the URL appears suspicious or unfamiliar, do not proceed.
- Context Inconsistency:
Consider whether the QR code makes sense in its context. If you find a QR code in an unusual or irrelevant location, such as on an unofficial poster or in a random public place, it may be malicious. Legitimate QR codes are typically placed in appropriate and relevant contexts by reputable organizations.
- Immediate Actions Without Confirmation:
Some devices are set to automatically perform actions, like opening a website or downloading a file, upon scanning a QR code. If this happens without your explicit permission or confirmation, it can be a sign of a scam. Always adjust your device settings to require confirmation before taking any action after scanning a QR code.
- Unclear or Vague Purpose:
A legitimate QR code should have a clear and specific purpose. If a QR code lacks a description or explanation, or if it’s not clear why you should scan it, be cautious. Scammers often provide little to no information about what the QR code does to trick users into scanning it without understanding the risks.
- High-Pressure Tactics:
Scammers may use QR codes alongside messages that create a sense of urgency or pressure, such as claiming limited time offers, immediate prizes, or urgent security warnings. These high-pressure tactics are designed to rush you into scanning the QR code without thinking. If you encounter a QR code with such tactics, it’s best to avoid it.
5 Best Practices to Mitigate QR Code Phishing Risks
While identifying deceptive QR codes is crucial, a multi-layered approach offers the most comprehensive protection against QR code phishing attempts. Here are some best practices to bolster your security posture:
- Leverage Two-Factor Authentication (2FA): Whenever possible, implement 2FA on all online accounts, particularly those pertaining to financial institutions and social media platforms. This robust security measure adds a significant hurdle for attackers, even if they manage to steal your login credentials through a phishing scam.
- Maintaining a Security-Conscious Mindset: Approach QR codes originating from unexpected sources with a critical eye. Whether encountered in emails, social media posts, or physical locations, prioritize verification before scanning.
- Enhancing Mobile Device Security: Consider employing a reputable mobile security application on your smartphone. These applications can offer real-time protection against malicious websites and malware downloads potentially triggered by compromised QR codes.
- Verification Techniques for Enhanced Security: Train yourself to become a URL verification expert. Before clicking on any link displayed upon scanning a QR code, meticulously examine the displayed address. Look for inconsistencies, typos, or unfamiliar website names. If it appears suspicious, err on the side of caution and refrain from clicking.
- Understanding Application Permissions: When installing a QR code scanner app, take a moment to review the requested permissions and privacy policy with a critical eye. Be wary of applications demanding excessive permissions unrelated to their core functionality of scanning QR codes.
While QR codes offer a convenient way to access information, they can also be a gateway to cyber-attacks known as QR code phishing. To stay safe, be wary of unsolicited codes and those with suspicious appearances. Legitimate codes will be clear and lead to recognizable websites. Don’t enter sensitive information after scanning and consider using a secure scanner app that previews the destination URL. Implement two-factor authentication whenever possible and maintain a cautious mindset. Always double-check URLs before clicking, review app permissions, and utilize mobile security solutions. Remember, a healthy dose of skepticism is key to navigating the world of QR codes securely.









